Primary Domain Controller Menggunakan OpenLDAP dan Samba Khusus Centos 5.10
https://anapiscan.wordpress.com/2014/05/22/primary-domain-controller-menggunakan-openldap-dan-samba-khusus-centos-5-10/
Ganti SELINUX yang awalnya enforcing menjadi disabled
# cat /etc/sysconfig/selinux
# This file controls the state of SELinux on the system. # SELINUX= can take one of these three values: # enforcing - SELinux security policy is enforced. # permissive - SELinux prints warnings instead of enforcing. # disabled - SELinux is fully disabled. SELINUX=disabled # SELINUXTYPE= type of policy in use. Possible values are: # targeted - Only targeted network daemons are protected. # strict - Full SELinux protection. SELINUXTYPE=targeted
Sisipkan allow port firewall untuk ldap
# vim /etc/sysconfig/iptables
# vim /etc/sysconfig/iptables
-A RH-Firewall-1-INPUT -s 192.168.1.0/24 -m state --state NEW -p tcp --dport 389 -j ACCEPT -A RH-Firewall-1-INPUT -s 192.168.1.0/24 -m state --state NEW -p tcp --dport 636 -j ACCEPT
# cat /etc/hosts
# Do not remove the following line, or various programs
# that require network functionality will fail.
127.0.0.1 localhost.localdomain localhost
::1 localhost6.localdomain6 localhost6
192.168.1.2 topek.local topek
# hostname
serverku
serverku
Download packages di epel, karena repository bawaan tidak tersedia untuk install smbldap-tools
# wget https://dl.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm
# wget https://dl.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm
--2014-05-19 06:14:16-- https://dl.fedoraproject.org/pub/epel/5/i386/epel-release-5-4.noarch.rpm Resolving dl.fedoraproject.org... 209.132.181.26, 209.132.181.27, 209.132.181.23, ... Connecting to dl.fedoraproject.org|209.132.181.26|:443... connected. HTTP request sent, awaiting response... 200 OK Length: 12232 (12K) [application/x-rpm] Saving to: `epel-release-5-4.noarch.rpm.1' 100%[======================================================================================================>] 12,232 --.-K/s in 0.01s 2014-05-19 06:14:17 (1.18 MB/s) - `epel-release-5-4.noarch.rpm.1' saved [12232/12232]
# cat /etc/sysconfig/network-scripts/ifcfg-eth0
# Realtek Semiconductor Co., Ltd. RTL8169 PCI Gigabit Ethernet Controller DEVICE=eth0 BOOTPROTO=static BROADCAST=192.168.1.255 HWADDR=64:70:02:01:23:7C IPADDR=192.168.1.2 NETMASK=255.255.255.0 NETWORK=192.168.1.0 ONBOOT=yes
# rpm -ivh epel-release-5-4.noarch.rpm
warning: epel-release-5-4.noarch.rpm: Header V3 DSA signature: NOKEY, key ID 217521f6
Preparing... ########################################### [100%]
1:epel-release ########################################### [100%]
# yum install openldap openldap-clients openldap-servers nss_ldap samba samba-client samba-common
# yum –enablerepo=epel install smbldap-tools
# slappasswd
# yum –enablerepo=epel install smbldap-tools
# slappasswd
New password: 12345
Re-enter new password: 12345
{SSHA}j1ihyBt/PQRZfaNho0R1CshIV7ay8NhC
# vim /etc/openldap/slapd.conf
# # See slapd.conf(5) for details on configuration options. # This file should NOT be world readable. # include /etc/openldap/schema/core.schema include /etc/openldap/schema/cosine.schema include /etc/openldap/schema/inetorgperson.schema include /etc/openldap/schema/nis.schema include /etc/openldap/schema/samba.schema # Allow LDAPv2 client connections. This is NOT the default. allow bind_v2 # Do not enable referrals until AFTER you have a working directory # service AND an understanding of referrals. #referral ldap://root.openldap.org pidfile /var/run/openldap/slapd.pid argsfile /var/run/openldap/slapd.args # Load dynamic backend modules: # modulepath /usr/lib/openldap # Modules available in openldap-servers-overlays RPM package # Module syncprov.la is now statically linked with slapd and there # is no need to load it here # moduleload accesslog.la # moduleload auditlog.la # moduleload denyop.la # moduleload dyngroup.la # moduleload dynlist.la # moduleload lastmod.la # moduleload pcache.la # moduleload ppolicy.la # moduleload refint.la # moduleload retcode.la # moduleload rwm.la # moduleload smbk5pwd.la # moduleload translucent.la # moduleload unique.la # moduleload valsort.la # modules available in openldap-servers-sql RPM package: # moduleload back_sql.la # The next three lines allow use of TLS for encrypting connections using a # dummy test certificate which you can generate by changing to # /etc/pki/tls/certs, running "make slapd.pem", and fixing permissions on # slapd.pem so that the ldap user or group can read it. Your client software # may balk at self-signed certificates, however. # TLSCACertificateFile /etc/pki/tls/certs/ca-bundle.crt # TLSCertificateFile /etc/pki/tls/certs/slapd.pem # TLSCertificateKeyFile /etc/pki/tls/certs/slapd.pem # Sample security restrictions # Require integrity protection (prevent hijacking) # Require 112-bit (3DES or better) encryption for updates # Require 63-bit encryption for simple bind # security ssf=1 update_ssf=112 simple_bind=64 access to dn.base="" by self write by * auth access to attrs=userPassword by self write by * auth access to attrs=shadowLastChange by self write by * read access to * by * read by anonymous auth # Sample access control policy: # Root DSE: allow anyone to read it # Subschema (sub)entry DSE: allow anyone to read it # Other DSEs: # Allow self write access # Allow authenticated users read access # Allow anonymous users to authenticate # Directives needed to implement policy: # access to dn.base="" by * read # access to dn.base="cn=Subschema* read # access to * # by self write # by users read # by anonymous auth # # if no access controls are present, the default policy # allows anyone and everyone to read anything but restricts # updates to rootdn. (e.g., "access to * by * read") # # rootdn can always read and write EVERYTHING! ####################################################################### # ldbm and/or bdb database definitions ####################################################################### database bdb suffix "dc=topek,dc=local" rootdn "cn=Manager,dc=topek,dc=local" # Cleartext passwords, especially for the rootdn, should # be avoided. See slappasswd(8) and slapd.conf(5) for details. # Use of strong authentication encouraged. # rootpw secret # rootpw {crypt}ijFYNcSNctBYg rootpw {SSHA}j1ihyBt/PQRZfaNho0R1CshIV7ay8NhC # The database directory MUST exist prior to running slapd AND # should only be accessible by the slapd and slap tools. # Mode 700 recommended. directory /var/lib/ldap # Indices to maintain for this database #index objectClass eq,pres #index ou,cn,mail,surname,givenname eq,pres,sub #index uidNumber,gidNumber,loginShell eq,pres #index uid,memberUid eq,pres,sub #index nisMapName,nisMapEntry eq,pres,sub index objectClass eq index cn pres,sub,eq index sn pres,sub,eq index uid pres,sub,eq index displayName pres,sub,eq index uidNumber eq index gidNumber eq index memberUID eq index sambaSID eq index sambaPrimaryGroupSID eq index sambaDomainName eq index default sub # Replicas of this database #replogfile /var/lib/ldap/openldap-master-replog #replica host=ldap-1.example.com:389 starttls=critical # bindmethod=sasl saslmech=GSSAPI # authcId=host/ldap-master.example.com@EXAMPLE.COM
# cp /usr/share/doc/samba-3.0.33/LDAP/samba.schema /etc/openldap/schema/samba.schema
# cp /etc/openldap/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
# chown -R ldap:ldap /var/lib/ldap/DB_CONFIG
# chmod 600 /var/lib/ldap/DB_CONFIG
# cp /etc/openldap/DB_CONFIG.example /var/lib/ldap/DB_CONFIG
# chown -R ldap:ldap /var/lib/ldap/DB_CONFIG
# chmod 600 /var/lib/ldap/DB_CONFIG
# vim /etc/openldap/init.ldif
dn: dc=topek,dc=local objectclass: dcObject objectclass: organization dc: topek o: topek description: Samba LDAP topek Data Center dn: cn=Manager,dc=topek,dc=local objectClass: organizationalRole cn: Manager description: Directory Manager
# service ldap start
Starting slapd: [ OK ]
# chkconfig ldap on
# ldapadd -v -D “cn=Manager,dc=topek,dc=local” -x -w 12345 -f /etc/openldap/init.ldif
# ldapadd -v -D “cn=Manager,dc=topek,dc=local” -x -w 12345 -f /etc/openldap/init.ldif
ldap_initialize( ) add objectclass: dcObject organization add dc: topek add o: topek add description: Samba LDAP topek Data Center adding new entry "dc=topek,dc=local" modify complete add objectClass: organizationalRole add cn: Manager add description: Directory Manager adding new entry "cn=Manager,dc=topek,dc=local" modify complete
# chown -R ldap:ldap /var/lib/ldap/
# chmod -R 600 /var/lib/ldap/*
# chmod -R 600 /var/lib/ldap/*
# slapcat
dn: dc=topek,dc=local objectClass: dcObject objectClass: organization dc: topek o: topek description: Samba LDAP Topek Data Center structuralObjectClass: organization entryUUID: 1357fc18-73cf-1033-91ff-ab63ec6eeabf creatorsName: cn=Manager,dc=topek,dc=local createTimestamp: 20140519182810Z entryCSN: 20140519182810Z#000000#00#000000 modifiersName: cn=Manager,dc=topek,dc=local modifyTimestamp: 20140519182810Z dn: cn=Manager,dc=topek,dc=local objectClass: organizationalRole cn: Manager description: Directory Manager structuralObjectClass: organizationalRole entryUUID: 1358a9a6-73cf-1033-9200-ab63ec6eeabf creatorsName: cn=Manager,dc=topek,dc=local createTimestamp: 20140519182810Z entryCSN: 20140519182810Z#000001#00#000000 modifiersName: cn=Manager,dc=topek,dc=local modifyTimestamp: 20140519182810Z
# ldapsearch -x -b “dc=topek,dc=local”
# extended LDIF # # LDAPv3 # base with scope subtree # filter: (objectclass=*) # requesting: ALL # # topek.local dn: dc=topek,dc=local objectClass: dcObject objectClass: organization dc: topek o: topek description: Samba LDAP topek Data Center # Manager, topek.local dn: cn=Manager,dc=topek,dc=local objectClass: organizationalRole cn: Manager description: Directory Manager # search result search: 2 result: 0 Success # numResponses: 3 # numEntries: 2
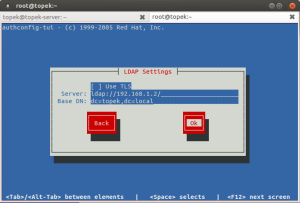
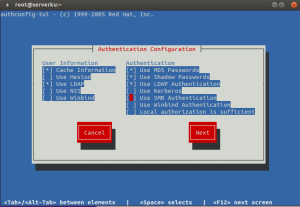
Setelah proses konfigurasi user lookup dan authentication selesai, maka service nscd akan otomatis restart seperti berikut.
# authconfig-tui
# authconfig-tui
Stopping nscd: [FAILED] Starting nscd: [ OK ]
# mv /etc/samba/smb.conf /etc/samba/smb.conf.bak
# cp /usr/share/doc/smbldap-tools-0.9.6/smb.conf /etc/samba/smb.conf
# cp /usr/share/doc/smbldap-tools-0.9.6/smb.conf /etc/samba/smb.conf
# vim /etc/samba/smb.conf
# Global parameters [global] workgroup = TOPEK netbios name = DATA-CENTER interfaces = eth0 server string = TOPEK security = user encrypt passwords = Yes bind interfaces only = No passdb backend = ldapsam:ldap://localhost client NTLMv2 auth = Yes client lanman auth = No client plaintext auth = No log level = 2 syslog = 1 log file = /var/log/samba/%m max log size = 0 smb ports = 139 445 name resolve order = wins time server = Yes server signing = auto add user script = /usr/sbin/smbldap-useradd -m '%u' add group script = /usr/sbin/smbldap-groupadd '%g' add user to group script = /usr/sbin/smbldap-groupmod -m '%u' '%g' set primary group script = /usr/sbin/smbldap-usermod -g '%g' '%u' add machine script = /usr/sbin/smbldap-useradd -w '%u' logon script = logon.bat logon drive = logon path = logon home = domain logons = Yes os level = 34 preferred master = Yes domain master = Yes wins support = Yes ldap admin dn = "cn=Manager,dc=topek,dc=local" ldap user suffix = ou=People ldap group suffix = ou=Group ldap idmap suffix = ou=Idmap ldap machine suffix = ou=Hosts ldap passwd sync = Yes ldap suffix = dc=topek,dc=local ldap ssl = no ldap timeout = 100 idmap backend = ldap:ldap://localhost idmap uid = 15000-20000 idmap gid = 15000-20000 winbind nested groups = Yes ea support = Yes map acl inherit = Yes inherit acls = Yes nt acl support = Yes force unknown acl user = Yes socket options = TCP_NODELAY SO_RCVBUF=8192 SO_SNDBUF=8192 SO_KEEPALIVE [Homes] comment = Home Directory %U, %u valid users = %U veto files = /*.mp3/*.wmv/*.avi/*.wma/*.wav/*.mpg/*.mpeg/*.mp4/*.MP3/*.WMV/*.AVI/*.WAV/*.MOV/*.MPG/*.MPEG/*.MP4/ delete veto files = Yes read only = No writable = Yes browseable = No guest ok = no create mask = 0700 directory mask = 0700 root preexec = /etc/samba/smb-preexec.sh "%u" "%g" [printers] comment = SMB Print Spool guest ok = No printable = No browseable = No use client driver = No disable spoolss = Yes load printers = No printing = none printcap name = /dev/null show add printer wizard = No guest account = nobody map to guest = Never [public] comment = Directory For Public path = /home/public hide dot files = yes read only = No force create mode = 0777 force directory mode = 0777 browsable = yes veto files = /*.mp3/*.wmv/*.avi/*.wma/*.wav/*.mpg/*.mpeg/*.mp4/*.MP3/*.WMV/*.AVI/*.WAV/*.MOV/*.MPG/*.MPEG/*.MP4/ delete veto files = Yes [teams] comment = Directory For Teams path = /home/teams hide dot files = yes read only = No force create mode = 0777 force directory mode = 0777 browsable = yes veto files = /*.mp3/*.wmv/*.avi/*.wma/*.wav/*.mpg/*.mpeg/*.mp4/*.MP3/*.WMV/*.AVI/*.WAV/*.MOV/*.MPG/*.MPEG/*.MP4/ delete veto files = Yes [netlogon] comment = Network Logon Service path = /home/netlogon browseable = No read only = No invalid users = root writable = Yes
# vim /etc/samba/smb-preexec.sh
#!/bin/sh
if [ ! -d "/home/$1" ]; then
mkdir -p "/home/$1"
chown -R "$1:$2" "/home/$1"
chmod 0700 "/home/$1"
fi
# vim /etc/pam.d/login
#%PAM-1.0 auth [user_unknown=ignore success=ok ignore=ignore default=bad] pam_securetty.so auth include system-auth account required pam_nologin.so account include system-auth password include system-auth # pam_selinux.so close should be the first session rule session required pam_selinux.so close session optional pam_keyinit.so force revoke session required pam_loginuid.so session include system-auth session optional pam_console.so # pam_selinux.so open should only be followed by sessions to be executed in the user context session required pam_selinux.so open session required pam_mkhomedir.so skel=/etc/skel/ umask=0077
# vim /etc/samba/smbusers
# Unix_name = SMB_name1 SMB_name2 ... root = administrator Administrator admin nobody = guest pcguest smbguest
Password samba dengan ldap harus sama.
# smbpasswd -w 12345
# smbpasswd -w 12345
Setting stored password for "cn=Manager,dc=topek,dc=local" in secrets.tdb
# service smb restart
Shutting down SMB services: [FAILED] Shutting down NMB services: [FAILED] Starting SMB services: [ OK ] Starting NMB services: [ OK ]
# service winbind restart
Shutting down Winbind services: [FAILED] Starting Winbind services: [ OK ]
# chkconfig smb on
# chkconfig winbind on
# chkconfig winbind on
# testparm
Load smb config files from /etc/samba/smb.conf
Processing section "[Homes]"
Processing section "[printers]"
Global parameter disable spoolss found in service section!
Global parameter load printers found in service section!
Global parameter printcap name found in service section!
Global parameter show add printer wizard found in service section!
Global parameter guest account found in service section!
Global parameter map to guest found in service section!
WARNING: [printers] service MUST be printable!
WARNING: No path in service printers - making it unavailable!
NOTE: Service printers is flagged unavailable.
Processing section "[public]"
Processing section "[teams]"
Processing section "[netlogon]"
Loaded services file OK.
Server role: ROLE_DOMAIN_PDC
Press enter to see a dump of your service definitions
# cp /etc/smbldap-tools/smbldap.conf /etc/smbldap-tools/smbldap.conf.bak
# net getlocalsid
SID for domain DATA-CENTER is: S-1-5-21-1331093182-1979255207-3456760660
SID for domain DATA-CENTER is: S-1-5-21-1331093182-1979255207-3456760660
# vim /etc/smbldap-tools/smbldap.conf
# $Id: smbldap.conf 35 2011-02-23 09:07:36Z fumiyas $ # # smbldap-tools.conf : Q & D configuration file for smbldap-tools # This code was developped by IDEALX (http://IDEALX.org/) and # contributors (their names can be found in the CONTRIBUTORS file). # # Copyright (C) 2001-2002 IDEALX # # This program is free software; you can redistribute it and/or # modify it under the terms of the GNU General Public License # as published by the Free Software Foundation; either version 2 # of the License, or (at your option) any later version. # # This program is distributed in the hope that it will be useful, # but WITHOUT ANY WARRANTY; without even the implied warranty of # MERCHANTABILITY or FITNESS FOR A PARTICULAR PURPOSE. See the # GNU General Public License for more details. # # You should have received a copy of the GNU General Public License # along with this program; if not, write to the Free Software # Foundation, Inc., 59 Temple Place - Suite 330, Boston, MA 02111-1307, # USA. # Purpose : # . be the configuration file for all smbldap-tools scripts ############################################################################## # # General Configuration # ############################################################################## # Put your own SID. To obtain this number do: "net getlocalsid". # If not defined, parameter is taking from "net getlocalsid" return #SID="S-1-5-21-2252255531-4061614174-2474224977" SID="S-1-5-21-1331093182-1979255207-3456760660" # Domain name the Samba server is in charged. # If not defined, parameter is taking from smb.conf configuration file # Ex: sambaDomain="IDEALX-NT" #sambaDomain="DOMSMB" sambaDomain="TOPEK" ############################################################################## # # LDAP Configuration # ############################################################################## # Notes: to use to dual ldap servers backend for Samba, you must patch # Samba with the dual-head patch from IDEALX. If not using this patch # just use the same server for slaveLDAP and masterLDAP. # Those two servers declarations can also be used when you have # . one master LDAP server where all writing operations must be done # . one slave LDAP server where all reading operations must be done # (typically a replication directory) # Slave LDAP server # Ex: slaveLDAP=127.0.0.1 # If not defined, parameter is set to "127.0.0.1" slaveLDAP="192.168.1.2" # Slave LDAP port # If not defined, parameter is set to "389" slavePort="389" # Master LDAP server: needed for write operations # Ex: masterLDAP=127.0.0.1 # If not defined, parameter is set to "127.0.0.1" masterLDAP="192.168.1.2" # Master LDAP port # If not defined, parameter is set to "389" masterPort="389" # Use TLS for LDAP # If set to 1, this option will use start_tls for connection # (you should also used the port 389) # If not defined, parameter is set to "0" ldapTLS="0" # Use SSL for LDAP # If set to 1, this option will use SSL for connection # (standard port for ldaps is 636) # If not defined, parameter is set to "0" ldapSSL="0" # How to verify the server's certificate (none, optional or require) # see "man Net::LDAP" in start_tls section for more details verify="require" # CA certificate # see "man Net::LDAP" in start_tls section for more details #cafile="/etc/pki/tls/certs/ldapserverca.pem" cafile="/etc/smbldap-tools/ca.pem" # certificate to use to connect to the ldap server # see "man Net::LDAP" in start_tls section for more details #clientcert="/etc/pki/tls/certs/ldapclient.pem" clientcert= "/etc/smbldap-tools/smbldap-tools.iallanis.info.pem" # key certificate to use to connect to the ldap server # see "man Net::LDAP" in start_tls section for more details #clientkey="/etc/pki/tls/certs/ldapclientkey.pem" clientkey="/etc/smbldap-tools/smbldap-tools.iallanis.info.key" # LDAP Suffix # Ex: suffix=dc=IDEALX,dc=ORG suffix="dc=topek,dc=local" # Where are stored Users # Ex: usersdn="ou=Users,dc=IDEALX,dc=ORG" # Warning: if 'suffix' is not set here, you must set the full dn for usersdn usersdn="ou=People,${suffix}" # Where are stored Computers # Ex: computersdn="ou=Computers,dc=IDEALX,dc=ORG" # Warning: if 'suffix' is not set here, you must set the full dn for computersdn computersdn="ou=Computers,${suffix}" # Where are stored Groups # Ex: groupsdn="ou=Groups,dc=IDEALX,dc=ORG" # Warning: if 'suffix' is not set here, you must set the full dn for groupsdn groupsdn="ou=Group,${suffix}" # Where are stored Idmap entries (used if samba is a domain member server) # Ex: idmapdn="ou=Idmap,dc=IDEALX,dc=ORG" # Warning: if 'suffix' is not set here, you must set the full dn for idmapdn idmapdn="ou=Idmap,${suffix}" # Where to store next uidNumber and gidNumber available for new users and groups # If not defined, entries are stored in sambaDomainName object. # Ex: sambaUnixIdPooldn="sambaDomainName=${sambaDomain},${suffix}" # Ex: sambaUnixIdPooldn="cn=NextFreeUnixId,${suffix}" sambaUnixIdPooldn="sambaDomainName=${sambaDomain},${suffix}" # Default scope Used scope="sub" # Unix password encryption (CRYPT, MD5, SMD5, SSHA, SHA, CLEARTEXT) hash_encrypt="SSHA" # if hash_encrypt is set to CRYPT, you may set a salt format. # default is "%s", but many systems will generate MD5 hashed # passwords if you use "$1$%.8s". This parameter is optional! crypt_salt_format="%s" ############################################################################## # # Unix Accounts Configuration # ############################################################################## # Login defs # Default Login Shell # Ex: userLoginShell="/bin/bash" userLoginShell="/bin/bash" # Home directory # Ex: userHome="/home/%U" userHome="/home/%U" # Default mode used for user homeDirectory userHomeDirectoryMode="700" # Gecos userGecos="System User" # Default User (POSIX and Samba) GID defaultUserGid="513" # Default Computer (Samba) GID defaultComputerGid="515" # Skel dir skeletonDir="/etc/skel" # Default password validation time (time in days) Comment the next line if # you don't want password to be enable for defaultMaxPasswordAge days (be # careful to the sambaPwdMustChange attribute's value) defaultMaxPasswordAge="99999" ############################################################################## # # SAMBA Configuration # ############################################################################## # The UNC path to home drives location (%U username substitution) # Just set it to a null string if you want to use the smb.conf 'logon home' # directive and/or disable roaming profiles # Ex: userSmbHome="\\PDC-SMB3\%U" userSmbHome="\\DATA-CENTER\%U" # The UNC path to profiles locations (%U username substitution) # Just set it to a null string if you want to use the smb.conf 'logon path' # directive and/or disable roaming profiles # Ex: userProfile="\\PDC-SMB3\profiles\%U" userProfile="\\DATA-CENTER\profiles\%U" # The default Home Drive Letter mapping # (will be automatically mapped at logon time if home directory exist) # Ex: userHomeDrive="H:" userHomeDrive="H:" # The default user netlogon script name (%U username substitution) # if not used, will be automatically username.cmd # make sure script file is edited under dos # Ex: userScript="startup.cmd" # make sure script file is edited under dos userScript="logon.bat" # Domain appended to the users "mail"-attribute # when smbldap-useradd -M is used # Ex: mailDomain="idealx.com" mailDomain="topek.local" ############################################################################## # # SMBLDAP-TOOLS Configuration (default are ok for a RedHat) # ############################################################################## # Allows not to use smbpasswd (if with_smbpasswd="0" in smbldap.conf) but # prefer Crypt::SmbHash library with_smbpasswd="0" smbpasswd="/usr/bin/smbpasswd" # Allows not to use slappasswd (if with_slappasswd="0" in smbldap.conf) # but prefer Crypt:: libraries with_slappasswd="0" slappasswd="/usr/sbin/slappasswd" # comment out the following line to get rid of the default banner # no_banner="1"
# vim /etc/smbldap-tools/smbldap_bind.conf
# $Id: smbldap_bind.conf 35 2011-02-23 09:07:36Z fumiyas $
#
############################
# Credential Configuration #
############################
# Notes: you can specify two differents configuration if you use a
# master ldap for writing access and a slave ldap server for reading access
# By default, we will use the same DN (so it will work for standard Samba
# release)
slaveDN="cn=Manager,dc=topek,dc=local"
slavePw="12345"
masterDN="cn=Manager,dc=topek,dc=local"
masterPw="12345"
# chmod -R 600 /etc/smbldap-tools/smbldap_bind.conf
# smbldap-populate
Populating LDAP directory for domain TOPEK (S-1-5-21-1331093182-1979255207-3456760660) (using builtin directory structure) entry dc=topek,dc=local already exist. adding new entry: ou=People,dc=topek,dc=local adding new entry: ou=Group,dc=topek,dc=local adding new entry: ou=Computers,dc=topek,dc=local adding new entry: ou=Idmap,dc=topek,dc=local adding new entry: uid=root,ou=People,dc=topek,dc=local adding new entry: uid=nobody,ou=People,dc=topek,dc=local adding new entry: cn=Domain Admins,ou=Group,dc=topek,dc=local adding new entry: cn=Domain Users,ou=Group,dc=topek,dc=local adding new entry: cn=Domain Guests,ou=Group,dc=topek,dc=local adding new entry: cn=Domain Computers,ou=Group,dc=topek,dc=local adding new entry: cn=Administrators,ou=Group,dc=topek,dc=local adding new entry: cn=Account Operators,ou=Group,dc=topek,dc=local adding new entry: cn=Print Operators,ou=Group,dc=topek,dc=local adding new entry: cn=Backup Operators,ou=Group,dc=topek,dc=local adding new entry: cn=Replicators,ou=Group,dc=topek,dc=local adding new entry: sambaDomainName=sambaDomain,dc=topek,dc=local entry sambaDomainName=TOPEK,dc=topek,dc=local already exist. Updating it... Please provide a password for the domain root: Changing UNIX and samba passwords for root New password: 12345 Retype new password: 12345
# mkdir /home/profiles
# mkdir /home/teams
# mkdir /home/public
# chmod -R 777 /home/*
# chgrp ‘Domain Users’ /home/*
# mkdir /home/netlogon
# chmod 777 /home/netlogon/
# mkdir /home/teams
# mkdir /home/public
# chmod -R 777 /home/*
# chgrp ‘Domain Users’ /home/*
# mkdir /home/netlogon
# chmod 777 /home/netlogon/
# vim /home/netlogon/logon.bat
net use H: "\\DATA-CENTER\Homes" net use N: "\\DATA-CENTER\public" net use O: "\\DATA-CENTER\teams"
# smbldap-useradd -a -m ‘luki’
# smbldap-passwd luki
# smbldap-passwd luki
Changing UNIX and samba passwords for luki New password: luki Retype new password: luki
# ldapsearch -b “ou=People,dc=topek,dc=local” -x “(uid=luki)”
# extended LDIF
#
# LDAPv3
# base with scope subtree
# filter: (uid=luki)
# requesting: ALL
#
# luki, People, topek.local
dn: uid=luki,ou=People,dc=topek,dc=local
objectClass: top
objectClass: person
objectClass: organizationalPerson
objectClass: inetOrgPerson
objectClass: posixAccount
objectClass: shadowAccount
objectClass: sambaSamAccount
cn: luki
sn: luki
givenName: luki
uid: luki
uidNumber: 1000
gidNumber: 513
homeDirectory: /home/luki
loginShell: /bin/bash
gecos: System User
sambaLogonTime: 0
sambaLogoffTime: 2147483647
sambaKickoffTime: 2147483647
sambaPwdCanChange: 0
displayName: luki
sambaSID: S-1-5-21-1331093182-1979255207-3456760660-3000
sambaLMPassword: EDC73F4A05671D05AAD3B435B51404EE
sambaAcctFlags: [U]
sambaNTPassword: 384030CAA2DFF383A93D6A344E10CD1D
sambaPwdLastSet: 1400532801
sambaPwdMustChange: 10040446401
shadowLastChange: 16209
shadowMax: 99999
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
# id luki
uid=1000(luki) gid=513(Domain Users) groups=513(Domain Users)
Masuk ke windows XP:
Setting DNS Server dan WINS Server ke IP 192.168.1.2
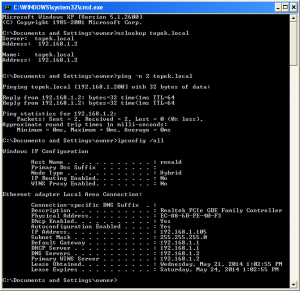
Setting computer name menjadi Ronald kemudian restart
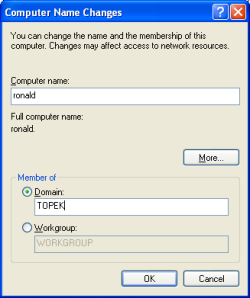
Setting domain menjadi TOPEK (mungkin huruf kecil/besar berpengaruh)
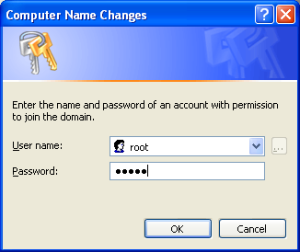
Login user : root
pass : 12345
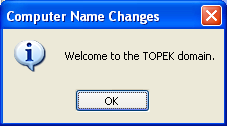
Jika berhasil, muncul Welcome to the TOPEK domain
Restart
Setting DNS Server dan WINS Server ke IP 192.168.1.2

Setting computer name menjadi Ronald kemudian restart

Setting domain menjadi TOPEK (mungkin huruf kecil/besar berpengaruh)
Login user : root
pass : 12345

Jika berhasil, muncul Welcome to the TOPEK domain

Restart
Sumber disini