If you are attempting to upgrade your vCenter Server and are getting stuck in stage one while connecting to the source appliance, a simple password change may get you going again. In my case, I was upgrading from vCenter 6.7 U2 to 7.0 but this could certainly occur with other upgrade paths as well. I got the following error:
“A problem occurred while getting data from the source vCenter Server.”
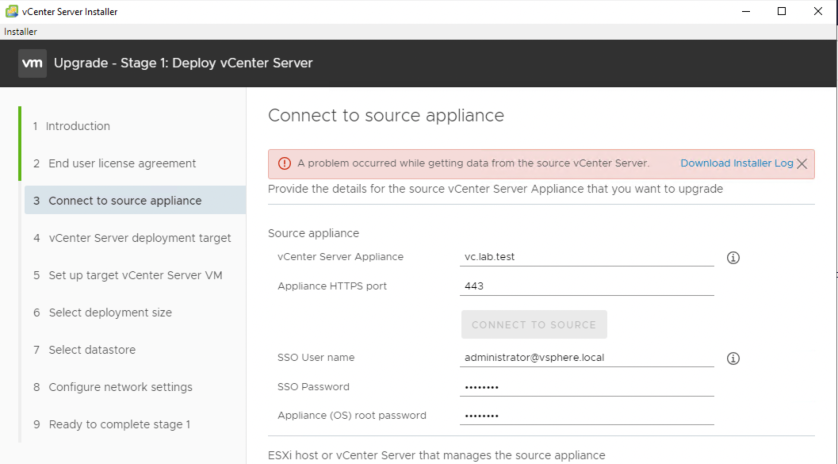
The error message is pretty non-descript, but we do get the option to download some logging. In the log file downloaded, it seems pretty clear that this is an authentication problem:
=======================================================
How to bypass BAD PASSWORD: it is based on a dictionary word for vCenter VCSA root account
Today I am midway through setting up my lab and realized the reason VMware Cloud Foundation (VCF) is failing is because I set the wrong password in my JSON file for the root account on my vCenter appliance.
No big deal, right? Just SSH in and change it. I tried, and got this:
| New password: BAD PASSWORD: it is based on a dictionary word passwd: Authentication token manipulation error passwd: password unchanged |
The bypass was actually easy. Presumably you’re already SSH’d in as root, so you just need to edit /etc/pam.d/system-password
| # Begin /etc/pam.d/system-password # use sha512 hash for encryption, use shadow, and try to use any previously # defined authentication token (chosen password) set by any prior module password requisite pam_cracklib.so dcredit=-1 ucredit=-1 lcredit=-1 ocredit=-1 minlen=6 difok=4 enforce_for_root password required pam_pwhistory.so debug use_authtok enforce_for_root remember=5 password required pam_unix.so sha512 use_authtok shadow try_first_pass # End /etc/pam.d/system-password |
Remove enforce_for_root from the first line with pam_cracklib.so. Save the file,
| # Begin /etc/pam.d/system-password # use sha512 hash for encryption, use shadow, and try to use any previously # defined authentication token (chosen password) set by any prior module password requisite pam_cracklib.so dcredit=-1 ucredit=-1 lcredit=-1 ocredit=-1 minlen=6 difok=4 password required pam_pwhistory.so debug use_authtok enforce_for_root remember=5 password required pam_unix.so sha512 use_authtok shadow try_first_pass # End /etc/pam.d/system-password |
no need to restart any services, and retry passwd.
| New password: BAD PASSWORD: it is based on a dictionary word Retype new password: passwd: password updated successfully |
After that, I re-added enforce_for_root to the file and clicked RETRY back in VCF and all things are happy once again.
===============================

Tidak ada komentar:
Posting Komentar