Single Sign-On Quick Start Guide for Admin
What is Synology Single Sign-On?
A user authentication solution that provides a single sign-on architecture to integrate all your web applications. Synology SSO allows businesses to protect web applications while simplifying authentication management.
Why use Synology Single Sign-On?
- Your sign-in experience is made safe and easy due to secure user authentication and faster access to all your web applications with a single sign-in per day.
- SSO lowers the need for IT help desk support for forgotten passwords by simplifying username and password management for convenience.
Scenario Overview
This SSO Quick Start Guide is designed for you to seamlessly access web applications installed on multiple Synology NAS devices within a single domain. By providing a workable scenario for dealing with SSO setup, you will be able to quickly adopt the configuration methods into your actual SSO setup. Each step process is based on this Scenario Overview to ensure that you can follow the process flow efficiently.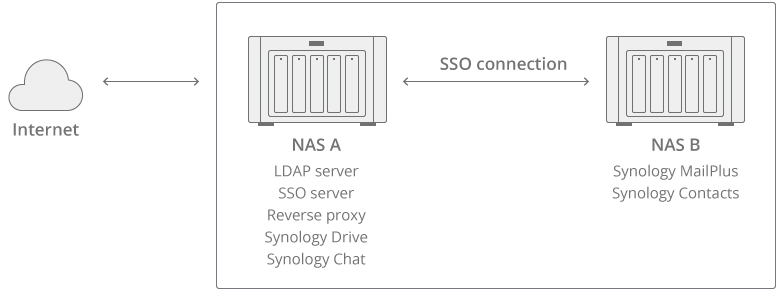
Environment
There are two Synology NAS devices used within the network with only one external IP.
- NAS A: Hosts LDAP Server, SSO Server, Synology Drive, and Synology Chat.
- NAS B: Hosts Synology MailPlus and Synology Contacts.
- The scenario provided uses the HTTPS protocol.
In the following configuration sequence, we will introduce how to configure login portals for different services, use a reverse proxy to set up a single entry point, and set up SSO to eliminate multiple sign-in efforts.
Before you start
- The process of joining your Synology NAS device to a directory service must be in place. Please refer to this article (for DSM 6.2 or DSM 7.0) on how to join an LDAP or a domain.
- Obtaining a valid certification of your Synology NAS devices should be in place. We encourage you to use Let’s Encrypt.
- Application services (e.g., Synology Drive, Synology Office, Synology Chat, etc.) must be installed and running on your Synology NAS devices.
- Port forwarding settings must be readily accessible to the Internet. Please be reminded that private IP addresses assigned to your Synology NAS device are not readily accessible via the Internet. Refer to this article for port forwarding rules configuration.
Configure login portals
Login portal provides access to supported Synology application services. You can skip the conventional DSM desktop sign-in process and directly access each application service with login portals.
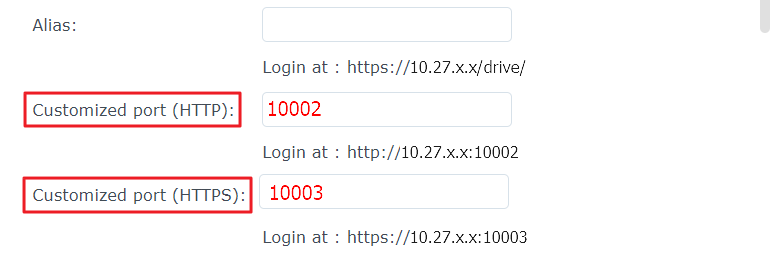
For the benefit of having a more practical explanation, we will set up login portals by using the following default port settings:
Synology NAS A | |
|---|---|
Application services | Default customized port (HTTP/HTTPS) |
Synology Drive Server | 10002/10003 |
Synology Chat Server | 20000/20001 |
Synology NAS B | |
|---|---|
Application services | Default customized port (HTTP/HTTPS) |
Synology MailPlus | 21680/21681 |
Synology Contacts1 | 25555/25556 |
Set and configure your applications to default customized ports.
- Go to the Control Panel of each of the NAS devices > Application Portal for DSM 6.2 or Control Panel > Login Portal > Applications for DSM 7.0.
- Select each application based on the table provided (e.g., Synology Drive Server), and click Edit > General for DSM 6.2 or Edit > Web Services for DSM 7.0 to set the port base on the application portal.
Use reverse proxy to set up a single entry point
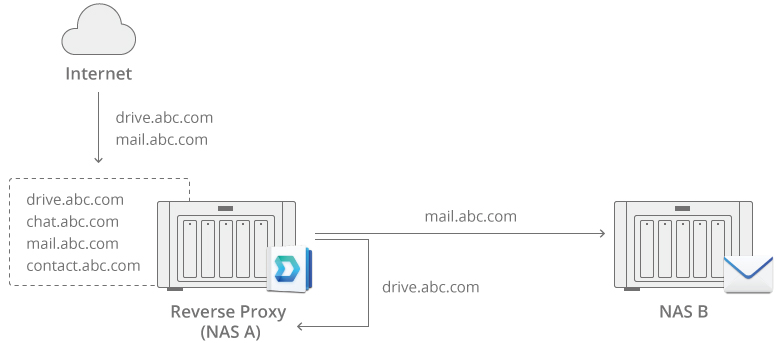
A reverse proxy server transfers requests from the Internet to devices on the local network. So if you have multiple Synology NAS devices on your LAN, the reverse proxy makes sure that external requests are routed to the right Synology NAS device.
To set up reverse proxy rules
- Go to the Control Panel of NAS A > Application Portal > Reverse Proxy > Create > General for DSM 6.2 or Control Panel > Login Portal > Advanced > Reverse Proxy > Create > General for DSM 7.0, and specify the following settings in the General page:
- If the FQDN is not provided by your DDNS service provider (e.g., abc.com), you must first ensure that the FQDN is resolved to the correct IP (NAS A's external IP). Each FQDN must have a valid certificate for the HTTPS connection.
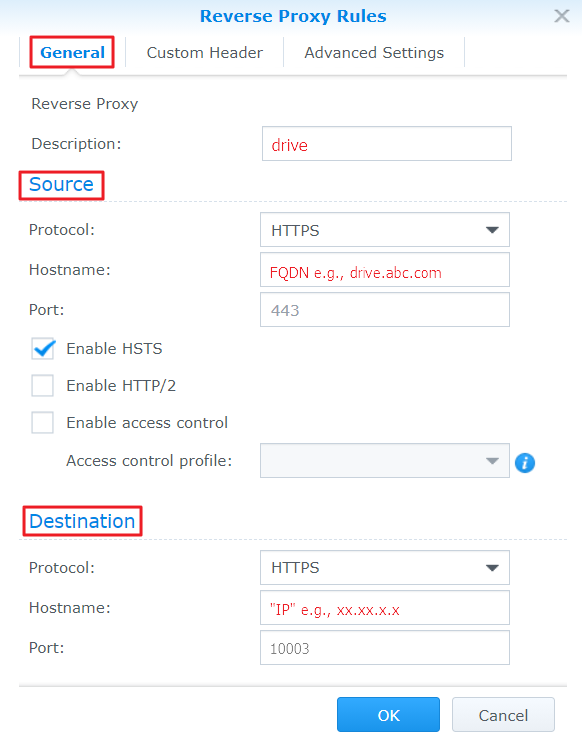
- Specify the rules for the Source (the device receiving requests from the Internet) and Destination (the device in the local network that the source device forwards requests to):
- Hostname: The name of the source/destination device.
- Source: The FQDN on the source device that leads to the (port-based) application portal on the destination device. e.g., "drive.abc.com" to enter the File Station portal.
- Destination: The IP of the destination device.
- Port: The port used by the source/destination device.
- Click Save for DSM 6.2 or OK for DSM 7.0 to save the settings.
To learn more about other recommended reverse proxy configurations, please refer to this section.
Identify SSO server through Application ID and URL
The SSO server must be linked to each of your Synology NAS devices to authenticate the users and provide faster access to your application services while utilizing Synology SSO.
- Go to the SSO Server of NAS A > Application List.
- Click Add, and a window will appear.
- Enter the name of the application in Application Name. In Redirect URI, enter the complete FQDN and port of the NAS device.
- Application Name: Name of the SSO client (NAS A and B) user e.g., peter dsm.
- Redirect URI: FQDN of the SSO client (NAS A and B) e.g., https://xxx.abc.com.
- Press OK to finish.
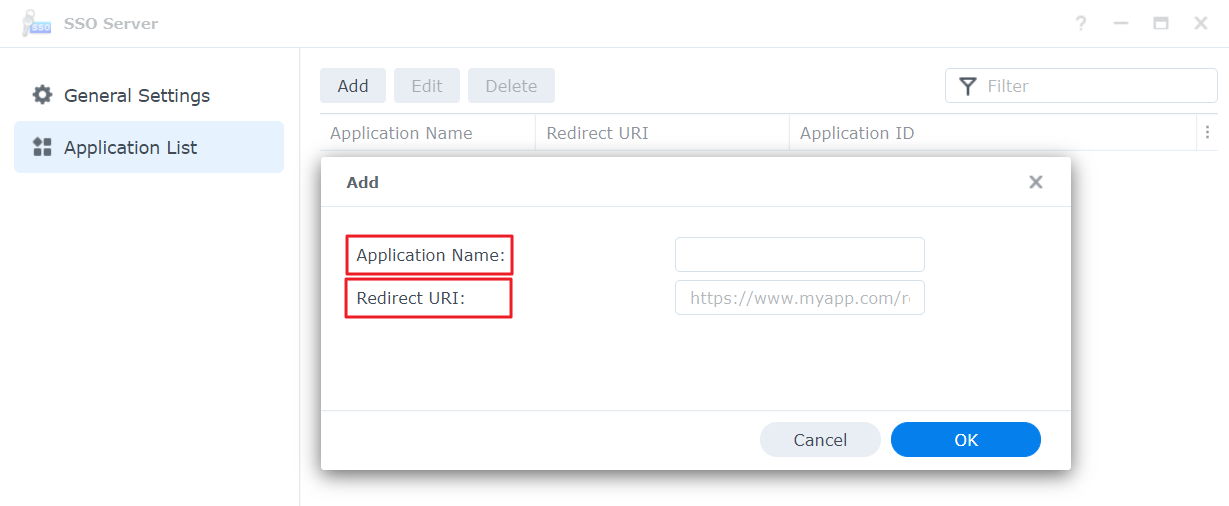
The SSO server will allocate an Application ID to the added application, and you can copy the Application ID for the SSO client setup.
Notes:
- SSO client applications must join the same domain or use the same LDAP service with the SSO server.
- SSO client applications must be on the same domain as the URI you specified in Redirect URI.
- All redirected URIs must use the same protocol as the SSO Server to ensure normal operation. We encourage you to use HTTPS for the security of data between the client and the web browser.
Match the SSO server to SSO client
To successfully establish centralized authentication using Synology SSO, the SSO server must be linked to its SSO clients.
Both NAS A and B servers need to configure the SSO client, please refer to the following steps below:
- Go to the Control Panel > Domain/LDAP > SSO Client > Synology SSO Service.
- Tick the Enable Synology SSO service, and enter the SSO server’s URL and the Application ID you have established in Identify SSO Server through Application ID and URL.
- SSO server URL: Enter SSO server’s FQDN and port (e.g., https://xxx.abc.com:5001). If you have enabled "Enable default port" - (help file) on the SSO server, please use port number 443 (HTTPS).
- Application ID: SSO Server > Application List > Application ID.
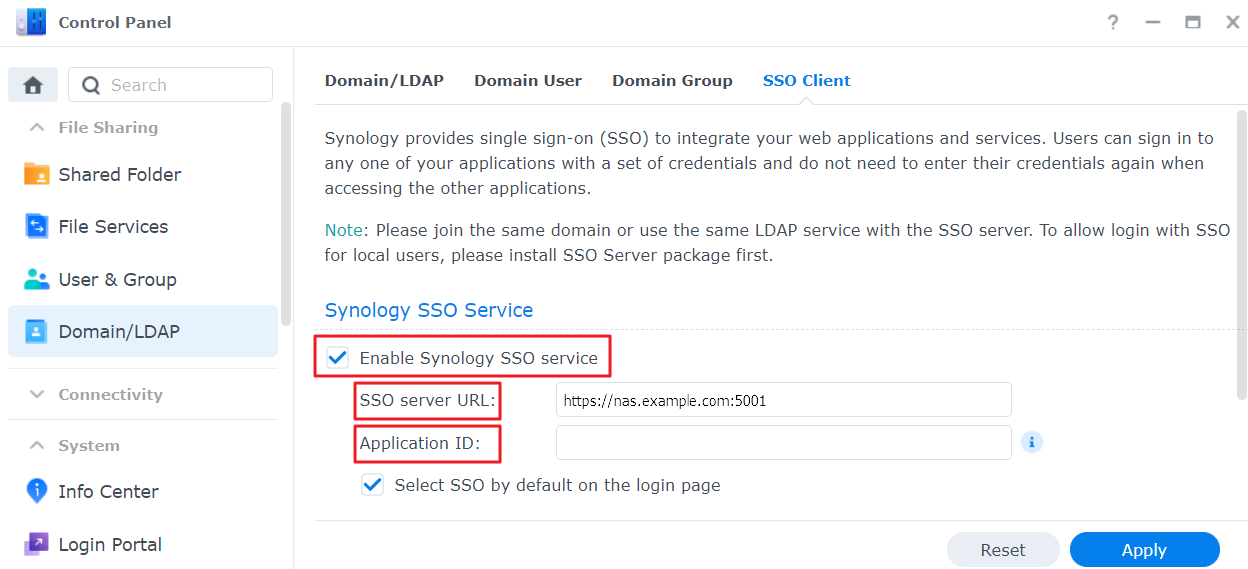
- Tick the Select SSO by default on the login page checkbox.
- Press Apply to finish.
Please make sure that the SSO server URL is successfully connected from the external network.
Configuration considerations and recommendations
Reverse proxy deployment
- Set up reverse proxy rules on the Synology NAS device that is less busy. For example, the Synology NAS device running MailPlus Server is generally busy. It is recommended to set up reverse proxy rules on another Synology NAS device without the mail service.
- Minimize the number of ports that are open in the port forwarding settings on the router for convenience and security.
- If a reverse proxy is not used and only the customized ports are configured in Login Portal, you will have to open two ports on the router for each application.
- If you decide to set up a reverse proxy, you'll need to utilize a customized port in the Application Portal. Alias and customized domain are not available as alternatives.
- In case you want to redirect HTTP requests to HTTPS requests automatically via Reverse Proxy, select HTTPS for both source and destination protocols, and tick the Enable HSTS checkbox.
Port forwarding with reverse proxy
Port forwarding routes the ports directly to a server, whereas reverse proxy communicates with other backend servers through the use of FQDN. This configuration reduces the number of ports exposed to the Internet that enhances security and saves you from the hassle of opening additional ports on the router.
Scenario:
Open port 443 (HTTPS) on an external IP and forward the port to NAS A server, and the reverse proxy will relay traffic to other backend servers through the FQDN of a service (e.g., drive.abc.com).
- When the reverse proxy and Login Portal are configured properly, you may connect to all the applications (supported by the Login Portal) and DSM customized domain on a single port 443.
Using the scenario above, you can connect to individual services through the FQDN of each service from an external network, but all of the following services must sign in individually due to the different domains, which requires the importation of SSO. Refer to this section for the procedure.
To learn more about reverse proxy rules, please refer to this article for DSM 7.0 or DSM 6.2.
Further reading
Software specs
- Full software specifications for SSO Server can be found here.
Related articles
- What network ports are used by DSM services?
- How do I set up a DNS server on my Synology NAS?
- For more SSO Server related articles, you can visit this page.
Tidak ada komentar:
Posting Komentar