Install GLPI ITSM Tool on CentOS 8
Welcome to our tutorial on how to install GLPI ITsM tool on CentOS 8. GLPI is an acronym for Gestionnaire Libre de Parc Informatique (Open Source IT Equipment Manager). It is a Free Asset and IT Management Software package, ITIL Service Desk, licenses tracking and software auditing tool.
GLPI provides a lot of advanced features for inventory, asset and mobile devices management. Read more GLPI features page.
Install GLPI ITSM Tool on CentOS 8
Prerequisites
GLPI is a web application and thus requires the basic components of LAMP/LEMP stack. In this demo, we are using LAMP Stack and thus;
Install and enable Remi repos as they provide some of the required PHP modules.
dnf install epel-release
dnf install https://rpms.remirepo.net/enterprise/remi-release-8.rpm
Enable Remi Repos for PHP 7.4.
dnf module reset php
dnf module enable php:remi-7.4
Execute the command below to install all GLPI LAMP stack requirements;
Note, GLPI requires PHP > 5.6, MySQL > 5.6 or MariaDB > 10.0.
dnf update
dnf install httpd mariadb-server php php-{curl,fileinfo,gd,json,mbstring,mysqli,session,zlib,simplexml,xml,cli,domxml,imap,ldap,openssl,xmlrpc,pecl-apcu} wget tar zip bzip2You can check our other guides on setting up LAMP/LEMP stack on CentOS 8.
Install LAMP Stack on CentOS 8
Install LEMP Stack on CentOS 8
Configure PHP for GLPI
Edit the PHP configuration file, php.ini and ensure the following settings are in place.
vim /etc/php.ini
Set the Maximum amount of memory;
memory_limit = 128M
Enable file uploads;
file_uploads = On
Set Maximum execution time;
max_execution_time = 30
Disable session initialization on request startup.
session.auto_start = 0
Disable the use of trans sid.
session.use_trans_sid = 0
Create GLPI Database and Database User
In this demo, we are using MariaDB as our database server.
Start and enable MariaDB to run on system boot;
systemctl enable --now mariadb
Run the initial security script.
mysql_secure_installation
Login to MariaDB and create GLPi database. Be sure to replace the databse name used here accordingly.
mysql -u root -p
create database glpidb;
Next, create GLPI database user and grant all rights on GLPI database.
grant all on glpidb.* to glpiadmin@localhost identified by 'myP@ssw0rd';
Reload the privileges table and exit the database.
flush privileges;
quit
Download GLPI Installer
Navigate to GLPI downloads page or GLPI GitHub releases page and grab the latest stable release, which is v9.4.5 as of this writing. Get the link and pull it with wget command.
wget https://github.com/glpi-project/glpi/releases/download/9.4.5/glpi-9.4.5.tgz
Install GLPI on CentOS 8
GLPI is a ready made application and its installation is as easy as extracting the archive contents to the GLPI web root directory. In this demo, our GLPI web root directory is set to /var/www/html/glpi.
tar xzf glpi-9.4.5.tgz -C /var/www/html/
Verify the GLPI web root directory;
ls /var/www/html/
glpiSet the proper ownership and permissions on the GLPI web server configuration files.
chown -R apache:apache /var/www/html/glpi
chmod -R 755 /var/www/html/glpi
Create Apache configuration file for GLPI.
vim /etc/httpd/conf.d/glpi.conf
Make the appropriate substitutions in the configuration file to suit your environment.
<VirtualHost *:80>
ServerName glpi.kifarunix-demo.com
DocumentRoot /var/www/html/glpi
ErrorLog "/var/log/httpd/glpi_error.log"
CustomLog "/var/log/httpd/glpi_access.log" combined
<Directory> /var/www/html/glpi/config>
AllowOverride None
Require all denied
</Directory>
<Directory> /var/www/html/glpi/files>
AllowOverride None
Require all denied
</Directory>
</VirtualHost>To setup GLPI with TLS certificates install mod_ssl package.
dnf install mod_ssl
Edit the /etc/httpd/conf.d/ssl.conf configuration file and set the correct paths to the TLS certificate, the CA certificate, if any, and certificate key file.
vim +/SSLCertificateFile /etc/httpd/conf.d/ssl.conf
Note that the configs below are Self-Signed Certificates and hence, no CA certificate specified. Be sure to obtain your certificates from a trusted CA and make appropriate configs.
... SSLCertificateFile /etc/pki/tls/certs/server.crt ... SSLCertificateKeyFile /etc/pki/tls/private/server.key ...
Then enable HTTPS for GLPI by editing the GLPI Apache configuration file created above, You can as well enable HTTP-HTTPS redirection;
vim /etc/httpd/conf.d/glpi.conf
<VirtualHost *:80>
ServerName glpi.kifarunix-demo.com
DocumentRoot /var/www/html/glpi
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]
</VirtualHost>
<VirtualHost *:443>
ServerName glpi.kifarunix-demo.com
DocumentRoot /var/www/html/glpi
ErrorLog "/var/log/httpd/glpi_error.log"
CustomLog "/var/log/httpd/glpi_access.log" combined
<Directory> /var/www/html/glpi/config>
AllowOverride None
Require all denied
</Directory>
<Directory> /var/www/html/glpi/files>
AllowOverride None
Require all denied
</Directory>
SSLEngine on
SSLCertificateKeyFile /etc/pki/tls/private/server.key
SSLCertificateFile /etc/pki/tls/certs/server.crt
</VirtualHost>
Verify Apache configuration syntax.
httpd -t Syntax OK
If you moved SSL/TLS files to the specified directories instead of copying them, you need to correct the SELinux contexts on those files by running the command below;
restorecon -RvF /etc/pki
Start and enable Apache to run on system boot.
systemctl enable --now httpd
If firewall is running, allow external access to Apache.
firewall-cmd --add-port={80,443}/tcp --permanent
firewall-cmd --reloadConfigure other SELinux Permissions for GLPI
In our demo, SELinux is set on enforcing mode. Hence, run the commands below to set the SELinux permissions for GLPI.
setsebool -P httpd_unified 1 setsebool -P httpd_can_network_connect 1 setsebool -P httpd_graceful_shutdown 1 setsebool -P httpd_can_network_relay 1 setsebool -P nis_enabled 1 setsebool -P httpd_can_network_connect_db 1 setsebool -P httpd_can_sendmail on
Accessing GLPI Web Interface
You can now finalize the setup of GLPI from browser. Use the address, http://glpi-server-IP-or-Hostname.
Choose you installation language.
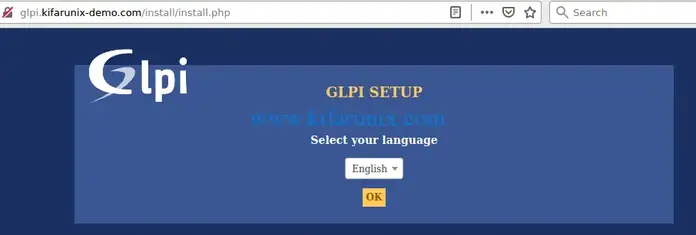
Accept the terms and conditions of GLPI license and click continue.
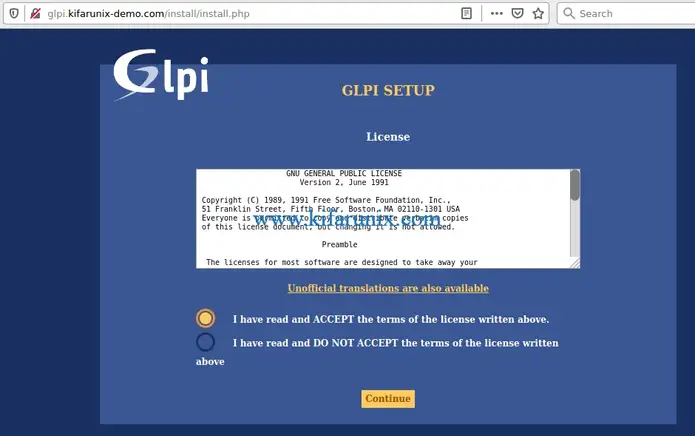
Click install, then verify that all prerequisites are met. Ignore the CAS extension warning if you are not using CAS authentication.
After all is set, proceed to configure Database connection settings;
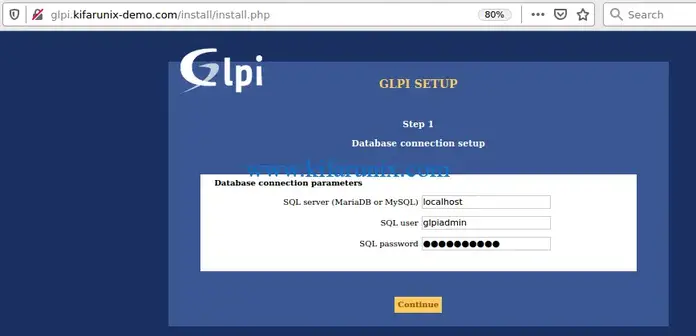
Choose your GLPI database.
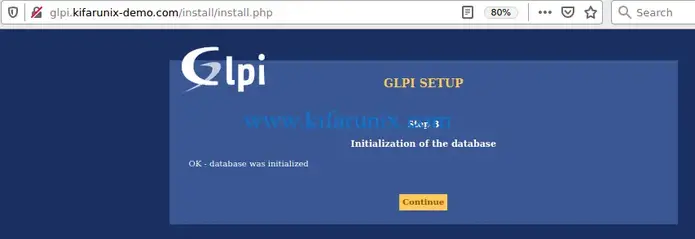
Wait for the database initialization to complete. Then click continue to follow through other steps and finally login to your GLPI web interface.

To login to GLPI web interface, there are a number of default user accounts you can use;
| Name | Username | Account Type |
| glpi | glpi | Admin account |
| tech | tech | Technical Account |
| normal | normal | Normal Account |
| post-only | postonly | Post only account |
Simply login as Admin, glpi and make the necessary changes including removing the default accounts above as well as resetting the password and username for GLPI admin user once you are logged in.
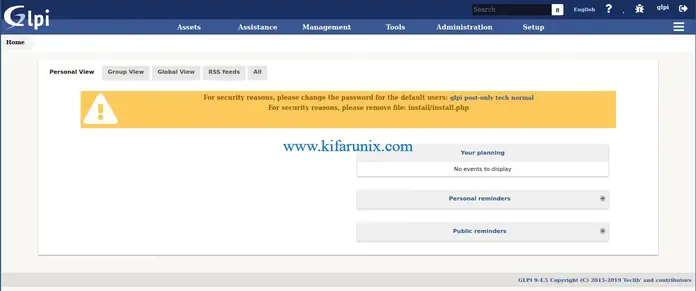
Remove installation file;
mv /var/www/html/glpi/install/install.php /var/www/html/glpi/install/install.php.old
There you go. You have successfully installed GLPI ITSM on CentOS 8. That brings us to the end of our guide on how to install GLPI ITSM tool on CentOS 8.
Reference

Tidak ada komentar:
Posting Komentar