What kind of malware is Ssoi?
We have discovered Ssoi while examining the samples submitted to the VirusTotal site. During the analysis, we found that Ssoi is ransomware that encrypts files, appends the ".ssoi" extension to filenames, and creates the "_readme.txt" file containing a ransom note. We also learned that Ssoi is part of the Djvu ransomware family.
An example of how Ssoi renames files: it changes "1.jpg" to "1.jpg.ssoi", "2.jpg" to "2.jpg.ssoi", and so forth.
Screenshot of files encrypted by Ssoi ransomware:
Ssoi ransom note overview
The ransom note contains contact and payment information. It instructs to email the attackers using support@sysmail.ch or supportsys@airmail.cc address. It mentions that the price ($980 or $490) of decryption software and key depends on how fast (within 72 hours or later) the attackers will be contacted.
More about ransomware
Access to files encrypted by ransomware can be restored without paying a ransom only when victims have a data backup up or a working third-party decryption tool. Usually, the attackers are the only ones who can decrypt files. Although, paying a ransom to them does not guarantee that they will provide a decryption tool.
It is strongly recommended not to pay a ransom and remove ransomware from the infected system to prevent it from causing further encryptions and computer infections. It is also advisable to always have files backed up on a remote server or unplugged storage device.
Ransomware in general
Ransomware encrypts files (and modifies their filenames) and generates a ransom note. Cybercriminals use it to blackmail victims. More ransomware examples are xSpace, Raf, Hfgd. Typically, the only main differences are the prices of decryption tools and encryption algorithms used to prevent victims from accessing files.
How did ransomware infect my computer?
We have discovered that Ssoi ransomware is distributed using a website offering to download videos from YouTube. That site displays a pop-up designed to download a malicious executable that encrypts files (infects computers with Ssoi ransomware).
In other cases, ransomware infects computers through malicious emails, files downloaded from untrustworthy sources, software cracking tools, fake updaters, Trojans. Either way, ransomware encrypts files after it (or a Trojan used to distribute it) is executed by users.
Emails used to distribute malware contain malicious attachments or links. Typically, they are disguised as important/official letters from legitimate entities. Examples of unreliable sources for downloading files/programs are unofficial pages, Peer-to-Peer networks, third-party downloaders, free file hosting sites.
Cracked software download pages are used to distribute malware too. Computers get infected after a malicious software cracking tool, or installer for pirated software is executed. It is important to mention that using pirated software is illegal. Fake updaters usually get downloaded from deceptive pages (for example, sites suggesting that the installed software is not up to date).
| Name | Ssoi virus |
| Threat Type | Ransomware, Crypto Virus, Files locker |
| Encrypted Files Extension | .ssoi |
| Ransom Demanding Message | _readme.txt |
| Free Decryptor Available? | Partial (more information below). |
| Ransom Amount | $980/$490 |
| Cyber Criminal Contact | support@sysmail.ch, supportsys@airmail.cc |
| Detection Names | Avast (Win32:RansomX-gen [Ransom]), Combo Cleaner (Trojan.GenericKDZ.85453), ESET-NOD32 (A Variant Of Win32/Kryptik.HOWN), Kaspersky (HEUR:Backdoor.Win32.Agent.gen), Microsoft (Ransom:Win32/Filecoder.GF!MTB), Full List Of Detections (VirusTotal) |
| Symptoms | Cannot open files stored on your computer, previously functional files now have a different extension (for example, my.docx.locked). A ransom demand message is displayed on your desktop. Cyber criminals demand payment of a ransom (usually in bitcoins) to unlock your files. |
| Distribution methods | Infected email attachments (macros), torrent websites, malicious ads, pop-up displayed by YouTube video download page |
| Damage | All files are encrypted and cannot be opened without paying a ransom. Additional password-stealing trojans and malware infections can be installed together with a ransomware infection. |
| Malware Removal (Windows) | To eliminate possible malware infections, scan your computer with legitimate antivirus software. Our security researchers recommend using Combo Cleaner. |
How to protect yourself from ransomware infections?
Do not open files/attachments (or website links) presented in irrelevant emails received from unknown, suspicious addresses. Always examine such emails before clicking links or opening files in them. Also, do not use unofficial websites and other unreliable sources to download files and programs. Download them from official pages and direct links.
Update and activate the installed software (and the operating system) using tools provided by its official developer. If your computer is already infected with Ssoi, we recommend running a scan with Combo Cleaner Antivirus for Windows to automatically eliminate this ransomware.
Screenshot of Ssoi's text file ("_readme.txt"):
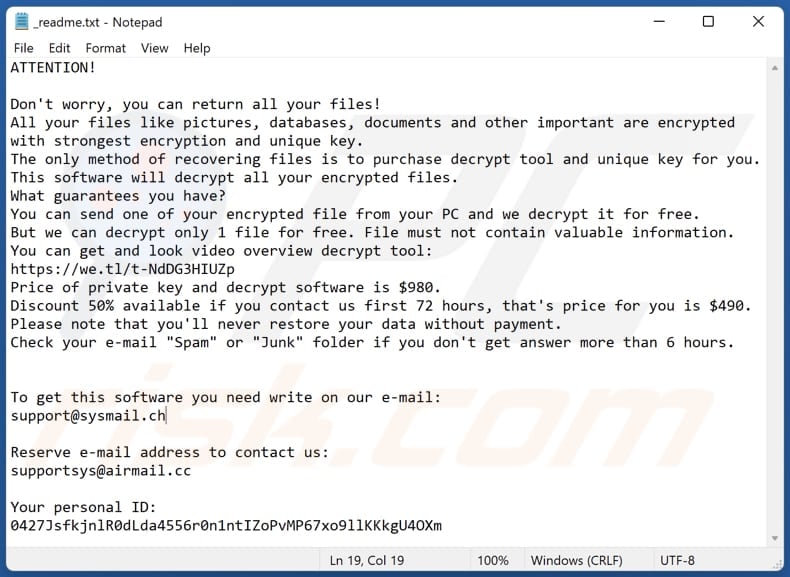
Text in the ransom note:
ATTENTION!
Don't worry, you can return all your files!
All your files like pictures, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-NdDG3HIUZp
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that's price for you is $490.
Please note that you'll never restore your data without payment.
Check your e-mail "Spam" or "Junk" folder if you don't get answer more than 6 hours.
To get this software you need write on our e-mail:
support@sysmail.chReserve e-mail address to contact us:
supportsys@airmail.ccYour personal ID:
-
Screenshot of a pop-up designed to download malicious executable (displayed by page supposedly functioning as YouTube video downloader):
There are currently two versions of Djvu ransomware infections: old and new. The old versions were designed to encrypt data by using a hard-coded "offline key" whenever the infected machine had no internet connection or the server was timing out/not responding.
Therefore, some victims were able to decrypt data using a tool developed by cyber security researcher, Michael Gillespie, however, since the encryption mechanism has been slightly changed (hence the new version, released in August, 2019), the decrypter no longer works and it is not supported anymore.
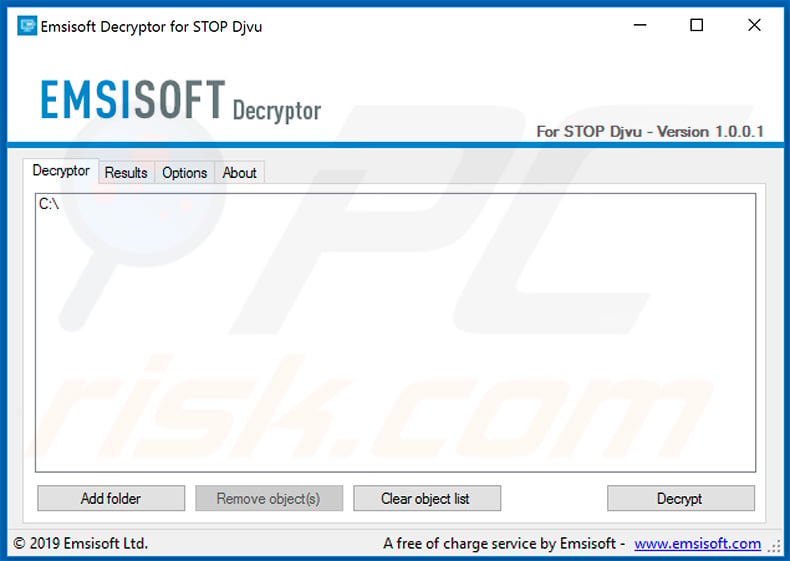
If your data has been encrypted by an older version, you might be able to restore it with the another tool developed by Emsisoft and Michael Gillespie. It supports a total of 148 Djvu's variants and you can find more information, as well as download link and decryption instructions in Emsisoft's official page.
Screenshot of Djvu decryption tool by Emsisoft and Michael Gillespie:
Additionally, Emsisoft is now providing a service that allows to decrypt data (again, only if it was encrypted by Djvu variants released before August, 2019) for those victims who have a pair of the same file before and after the encryption. All victims have to do is upload a pair of original and encrypted file to Emsisoft's Djvu decryption page and download the aforementioned decryption tool (the download link will be provided after uploading files).
Note that the file processing may take some time so be patient. It is also worth mentioning that the system must have an Internet connection during the entire decryption process, otherwise it will fail.
Screenshot of Emsisoft's Djvu decryption service page:
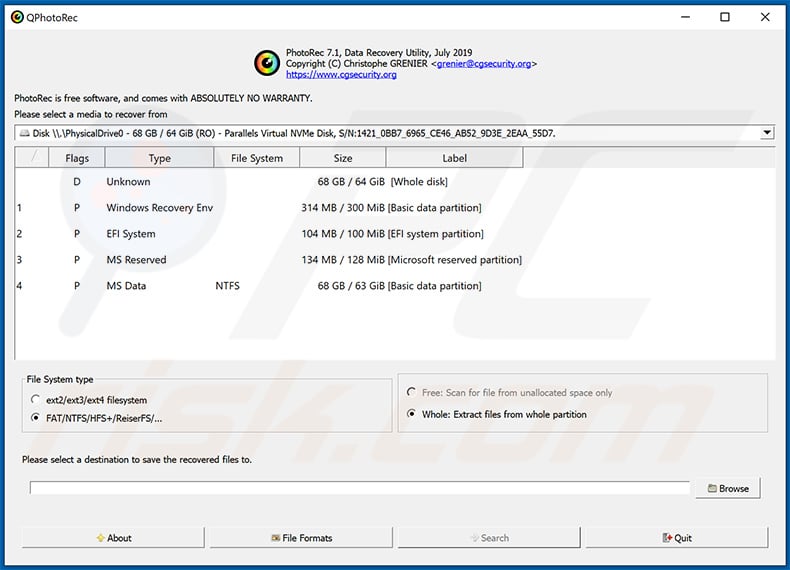
Some victims state that they've successfully restored a part of encrypted data using PhotoRec tool developed by CGSecurity (Christophe Grenier). You can download this tool from CGSecurity's official website.
Screenshot of PhotoRec application:
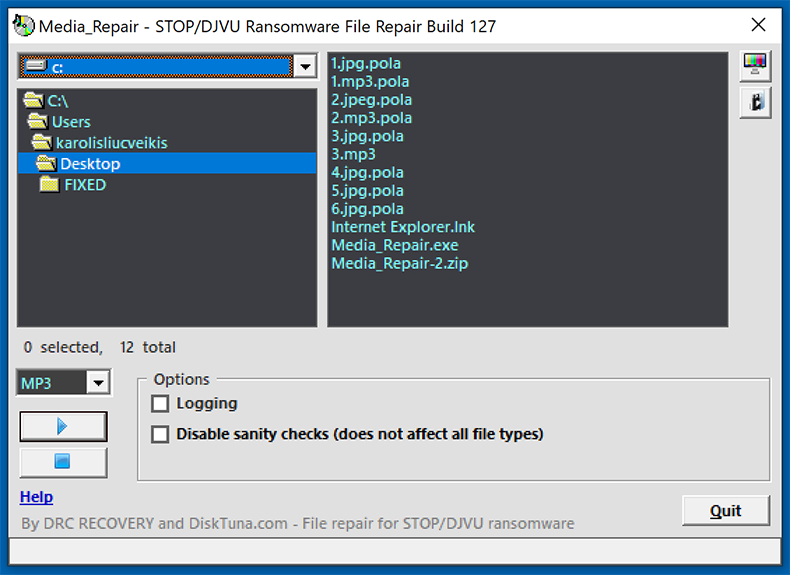
Now it is worth noting that Djvu ransomware does not encrypt the entire file. Instead, it encrypts only a portion (start) of the file, thereby making it unusable. Luckily, in some cases it is possible to restore other part of the file, which is not encrypted. This is useful when it comes to audio/video files, because even though the start won't be restored, you'll still be able to use most of it.
To restore audio/video data we advise you to use Media_Repair tool developed by DiskTuna. This tool is extremely simple and completely free. You can find the user manual as well as download the tool directly from DiskTuna's website.
Screenshot of Media_Repair application developed by DiskTuna:
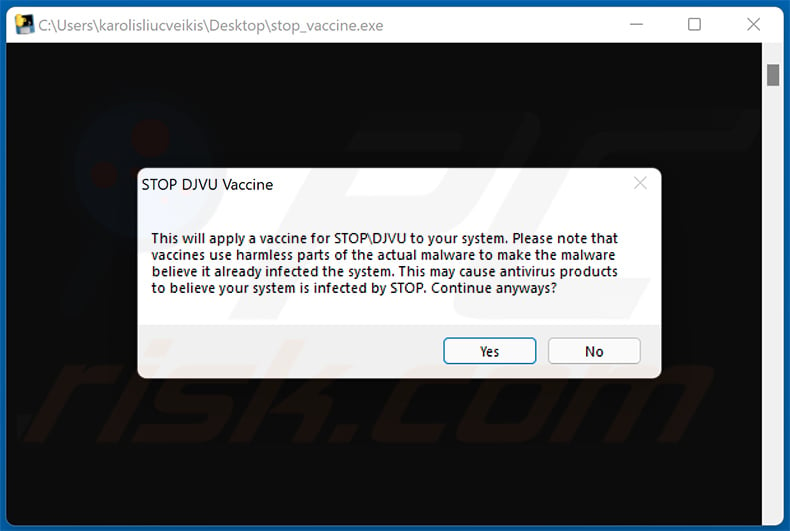
G DATA company has also released a "vaccine" capable of preventing Djvu ransomware from encrypting data. This does not mean that the malware won't be able to enter the system or to perform other actions (e.g., change system settings). However, the encryption will be prevented nevertheless. You can download the vaccination tool from this GitHub page.
Screenshot of G DATA's Djvu ransomware vaccination tool:
Ssoi ransomware removal:
Instant automatic malware removal:Manual threat removal might be a lengthy and complicated process that requires advanced IT skills. Combo Cleaner is a professional automatic malware removal tool that is recommended to get rid of malware. Download it by clicking the button below:
▼ DOWNLOAD Combo CleanerBy downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. To use full-featured product, you have to purchase a license for Combo Clea
Tidak ada komentar:
Posting Komentar