https://www.youtube.com/watch?v=vuzrihbet1E
As you may already know, Windows Server 2008 and 2008 R2 products reached End of Extended support on 1/14/2020. So if your Active Directory is running on Windows Server 2008, It is time to look for upgrade options.
In this blog post, I am going to demonstrate how to migrate Active Directory from Windows Server 2008 to Windows Server 2019.
AD Migration task itself is very straight forward. But there are other things you need to consider before you do an AD migration. Below I listed a checklist you can use on many occasions.
ACTIVE DIRECTORY MIGRATION CHECK LIST
• Evaluate business requirement for Active Directory migration
• Perform Audit on Existing Active Directory Infrastructure to make sure there are no existing health issues
• Provide Plan for implementation Process
• Prepare Physical / Virtual resources for Domain Controller
• Install Windows server 2019 Standard / Datacenter
• Patch Servers with latest Windows Updates
• Assign Dedicate IP address to Domain Controller
• Install AD DS Role
• Migrate Application and Server Roles from the Existing Domain Controllers.
• Migrate FSMO roles to new Domain Controllers
• Add New Domain controllers to the Existing Monitoring system
• Add New Domain controllers to the Existing DR Solution
• Decommission old domain controllers
• Raise the Domain and Forest Functional level
• On-Going Maintenance (Group Policy Review, New Features Implementations, Identify and fix active directory infrastructure issues)
If organizations running AD DS, it’s obvious it to have active directory integrated applications. Some of those may use it just for LDAP authentication and some may use advanced integration with modified active directory schema. with active directory migration, some of these applications may require modifications or upgrades to match with the new AD DS version. Therefor before the implementation process, it is important to recognize these active directory integrated applications and evaluate its impact on the migration.
LDAP Connection String Modifications – To use single-sign-on (SSO) with applications it may use LDAP connections to domain controllers. sometimes applications use hardcoded hostnames or IP addresses of domain controllers to define the connections. If domain migration involves IP address changes and Hostname changes, alternation to these records will be needed.
Schema Version Changes – Some legacy applications only support certain versions of active directory schema. This is specifically applying for custom made active directory integrated applications. This is very rare but I have to face these in my active directory migrations projects. Therefore if it’s not well-known applications, check with the application vendor if it supported new AD DS schema version.
Application Migrations – Some organizations have legacy application versions that no longer support or develop by its vendor. There are occasions where these types of issues turn to be bottlenecks for AD Migration projects. Once I was working on AD DS 2003 to AD DS 2012 R2 migration project. The organization had a legacy application that runs on windows server 2000 system. AD DS 2012 R2 does not support windows server 2000-member servers. The vendor who created the application no longer in business. Then we had to users to similar type application which supports new operating systems before we start the Active Directory migrations.
Server Roles/Applications installed on Domain Controllers – In the majority of the cases, once FSMO roles migrated to new domain controllers, old domain controllers will be decommissioned. Even though Microsoft recommends not to install applications or other server roles in domain controllers, people still do it. Some of the common roles installed in domain controllers are DHCP, File Servers, Licensing Server. If existing domain controllers are subject decommission these applications and server roles need to migrate new servers.
MOST COMMON QUESTIONS ABOUT ACTIVE DIRECTORY MIGRATIONS
In below I listed some of the most common questions I get about AD migration,
1. Can I keep the same IP address for the PDC? Yes, you can. Active Directory fully supports for IP address changes. Once FDMO role migration is completed, you can swap the IP addresses of Domain Controllers.
2. Can I downgrade forest/domain functional levels? Yes, you can do it from Windows server 2008 R2.
3. Do I need to migrate the DNS role? No, it is part of the AD. When you add a new domain controller, you can make it as DNS server too.
4. Do I need to change SYSVOL replication from FRS to DFS? If your domain is built based on Windows server 2008 or Windows Server 2008 R2, you are already using DFS for SYSVOL replication. If you originally migrated from Windows server 2003, it’s more likely you are still using FRS. In that case, after the migration, you can also change the SYSVOL replication method from FRS to DFS. I already have a blog post covering this topic https://www.rebeladmin.com/2015/04/step-by-step-guide-for-upgrading-sysvol-replication-to-dfsr-distributed-file-system-replication/
5. Can I keep Windows 2008 Domain Controllers and upgrade forest and domain functional level to Windows Server 2016? (Windows server 2019 does not have the forest and domain functional level name as Windows server 2019. it is still called Windows server 2016) – No, you can’t. Before forest and domain functional level upgrade, you need to decommission Windows server 2008 domain controllers.
DEMO ENVIRONMENT
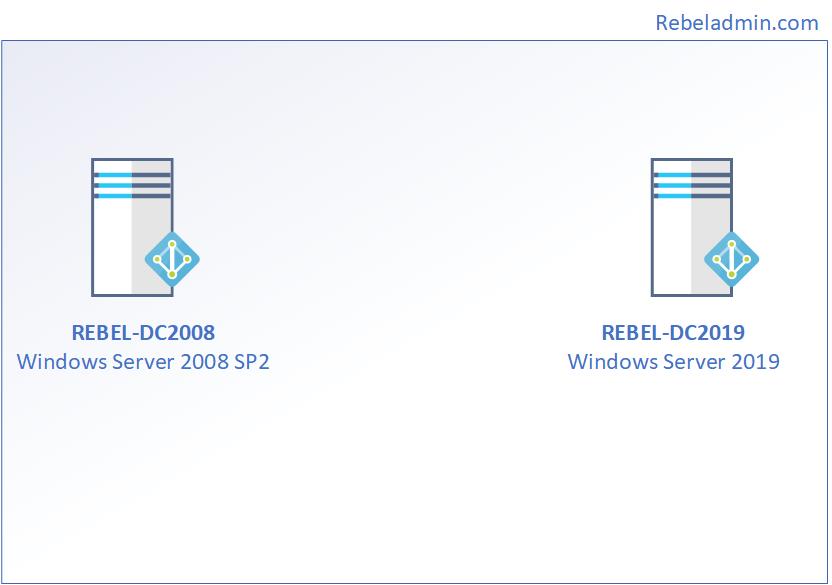
As per the above figure, rebeladmin.com domain has two domain controllers. The FSMO role holder (REBEL-DC2008) is running a domain controller based on windows server 2008. Domain and forest functional level currently operating at Windows server 2008. A new domain controller with Windows Server 2019 (REBEL-DC2019) will be introduced and it will be the new FSMO role holder for the domain. once FSMO role migration completed, Domain controller running windows server 2008 will be decommissioned. After that forest and domain, the functional level will be raised to the windows server 2019.
Note – When you introduce new domain controllers to the existing infrastructure it is recommended to introduce to the forest root level first and then go to the domain tree levels.
ADD WINDOWS SERVER 2019 DOMAIN CONTROLLER
As the first part of the configuration, we need to make REBEL-DC2019 as an Additional Domain Controller. To do that,
1. Log in to the Server as a member of the local administrators’ group.
2. Add server to the existing domain as a member.
3. Log in to the domain controller as an enterprise administrator.
4. Verify the static IP address allocation using ipconfig /all.
5. Launch the PowerShell Console as an Administrator
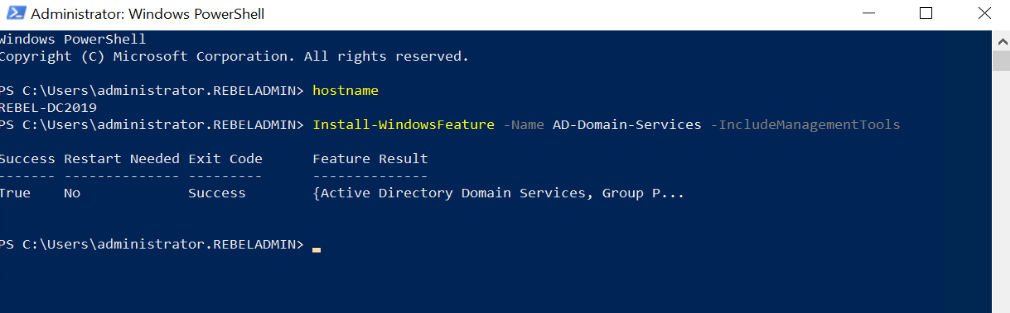
6. Before the configuration process, we need to install the AD DS Role in the given server. To do that we can use the following command.
Install-WindowsFeature –Name AD-Domain-Services -IncludeManagementTools
7. Configure the new server as an additional domain controller using,
Install-ADDSDomainController
-CreateDnsDelegation:$false
-InstallDns:$true
-DomainName “rebeladmin.com”
-SiteName “Default-First-Site-Name”
-ReplicationSourceDC “REBEL-DC2008.rebeladmin.com”
-DatabasePath “C:\Windows\NTDS”
-LogPath “C:\Windows\NTDS”
-SysvolPath “C:\Windows\SYSVOL”
-Force:$true
Note – There are no line breaks for the command and I have listed it as above to allow readers to focus on the parameters.
The following table explain the PowerShell arguments and what it will do.
| Argument | Description |
| Install-ADDSDomainController | This cmdlet will install the domain controller in active directory infrastructure. |
| -CreateDnsDelegation | Using this parameter can define whether to create DNS delegation that reference active directory integrated DNS. |
| -InstallDns | Using this can specify whether DNS role need to install with active directory domain controller. For new forest, it is default requirement to set it to $true. |
| -DomainName | This parameter defines the FQDN for the active directory domain. |
| -SiteName | This Parameter can use to define the active directory site name. the default value is Default-First-Site-Name |
| -ReplicationSourceDC | Using this parameter can define the active directory replication source. By default, it will use any available domain controller. But if need we can be specific. |
| -DatabasePath | This parameter will use to define the folder path to store active directory database file (Ntds.dit) |
| -LogPath | Log path can use to specify the location to save domain log files. |
| -SysvolPath | This is to define the SYSVOL folder path. Default location for it will be C:\Windows |
| -Force | This parameter will force command to execute by ignoring the warning. It is typical for the system to pass the warning about best practices and recommendations. |
Once execute the command it will ask for SafeModeAdministrator Password. Please use a complex password to proceed. This will be used for DSRM.
After the server is rebooted, log back in as an administrator to check the AD DS status.
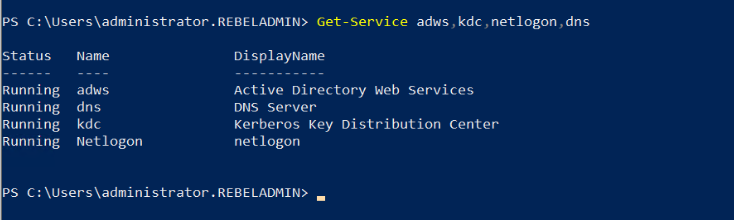
Get-Service adws,kdc,netlogon,dns
Will confirm the status of the AD DS service.
Then run following to confirm the current FSMO role holder.
$FormatEnumerationLimit =-1
Get-ADDomainController -Filter * | Select-Object Name, Domain, Forest, OperationMasterRoles | Where-Object {$_.OperationMasterRoles} | out-string -Width 160
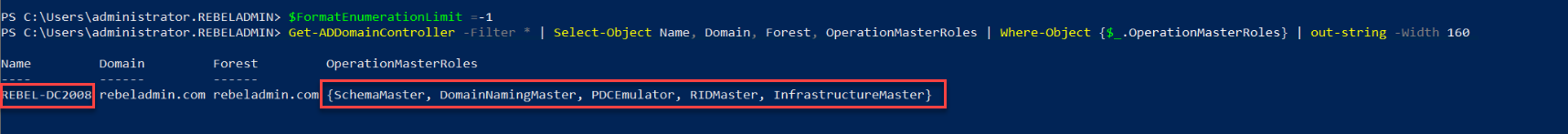
In the above, I used $FormatEnumerationLimit to show more data in output without truncating.
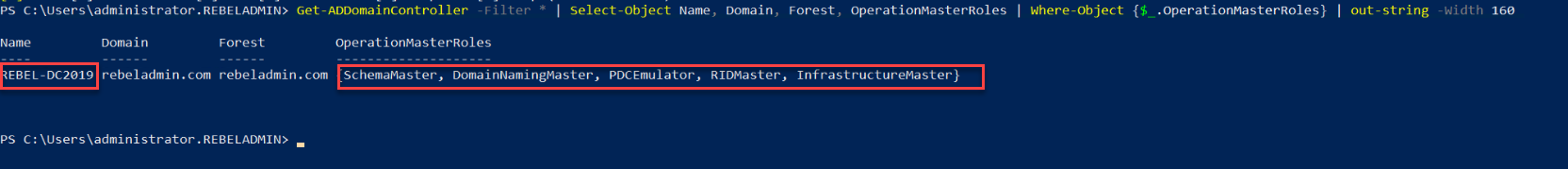
As we can see in output REBEL-DC2008 holds all five FSMO roles.
MOVE ACTIVE DIRECTORY FSMO ROLES
The next part of the migration is to move FSMO roles to the new Windows Server 2019 Domain controller (REBEL-DC2019).
We can do this by running,
Move-ADDirectoryServerOperationMasterRole -Identity REBEL-DC2019 -OperationMasterRole SchemaMaster, DomainNamingMaster, PDCEmulator, RIDMaster, InfrastructureMaster
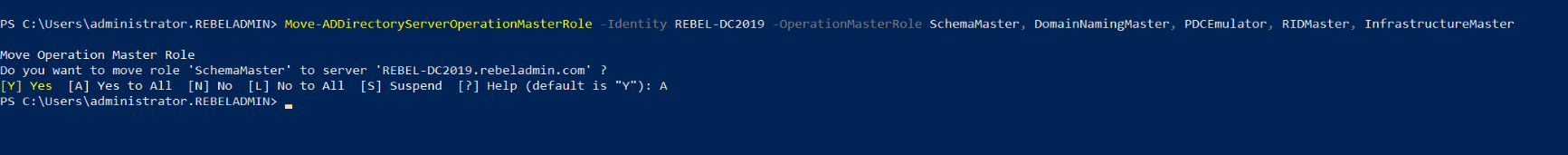
This command needs to run in the new windows 2019 domain controller as Enterprise Administrator.
Then rerun the following command to verify the new FSMO role owner.
Get-ADDomainController -Filter * | Select-Object Name, Domain, Forest, OperationMasterRoles | Where-Object {$_.OperationMasterRoles} | out-string -Width 160
DECOMMISSION OLD DOMAIN CONTROLLER
Now we moved FSMO roles over and the next step is to decommission old DC which is running with windows server 2008.
To do that,
1. log in to old DC as enterprise administrator
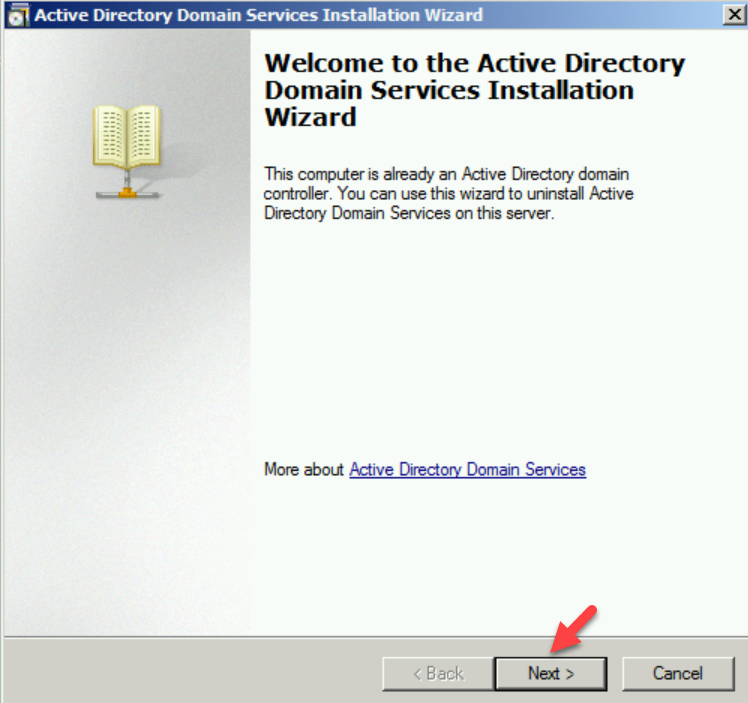
2. Go to Run | dcpromo
3. It will open up the dcpromo wizard. Click on Next to continue.
4. In the next page also click on Next.
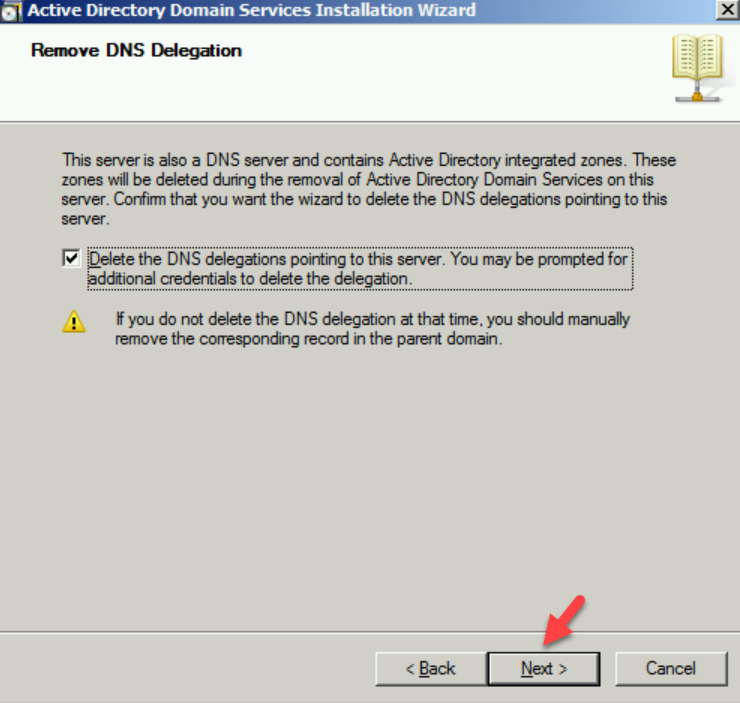
5. In Remove DNS Delegation page keep the default selection and click on Next.
6. Then the system will prompt for credentials. Provide Domain Admin credentials here.
7. On the next page, type a new password for the local administrator account.
8. In summary, page, click on Next to complete the process.
Once the process is completed, reboot the server.
RAISE DOMAIN AND FOREST FUNCTIONAL LEVEL
After you demote your last domain controller running with windows server 2008 we can raise Domain and Forest Functional level to windows server 2016 ( Windows server 2019 is the same).
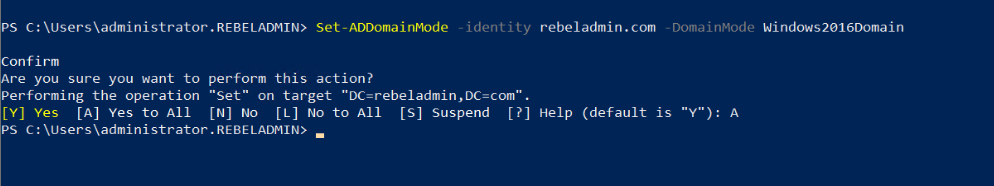
To upgrade the domain functional level, you can use the following PowerShell command in the Windows server 2019 domain controller.
Set-ADDomainMode –identity rebeladmin.com -DomainMode Windows2016Domain
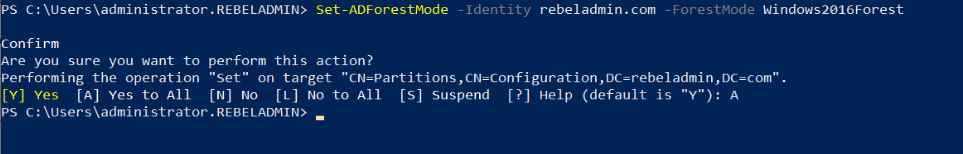
To upgrade the forest function level, you can use the following command
Set-ADForestMode -Identity rebeladmin.com -ForestMode Windows2016Forest
After the migration completes, we still need to verify if it completes successfully.
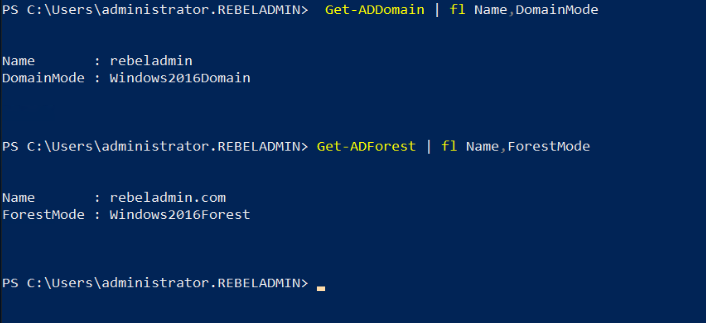
Get-ADDomain | fl Name,DomainMode
This command will show the current Domain functional level of the domain after the migration.
Get-ADForest | fl Name,ForestMode
The above command will show the current forest functional level of the domain.
This marks the end of this blog post. Hope now you know how to migrate Active Directory from Windows server 2008 to Windows Server 2019. If you have any questions feel free to contact me on rebeladm@live.com also follow me on twitter @rebeladm to get updates about new blog posts